The short: A newly discovered ransomware-delivering trojan for Apple's OS X operating system may have infected several thousand users over the weekend. The trojan, OS X.KeRanger.A, was delivered via a malicious build of the Mac OS X bittorrent client ‘Transmission’ and will begin encrypting victims' local files today after a 3 day waiting period.
This was a sophisticated watering hole attack that attempted to maximize its impact by delaying activation of the ransomware for three days. If the ransomware had activated immediately, the compromised installer would have been apparent at once. However, the malware was detected far faster than the criminals hoped, and prompt action by Apple has prevented a widespread impact. In fact, based on the timeline of events, it appears that Apple was so quick to respond that countermeasures were deployed to OS X's XProtect and Gatekeeper many hours before Transmission's owners were able to take down the malicious installers from their own website.
Timeline:
Around March 5th, blips of OS X users beginning noticing the first indicators of a new ransonware trojan targeting Mac users. That Saturday afternoon, Al Varnell (@Varnell) noted an update to Apple’s Protect service that added a signature for OS X.KeRanger.A, asking if anybody knew more. Later that evening a member of the Transmission forums posted stating that their newly installed version of Transmission 2.90 was flagged by OS X as containing malware.
https://twitter.com/alvarnell/status/706250783210106880
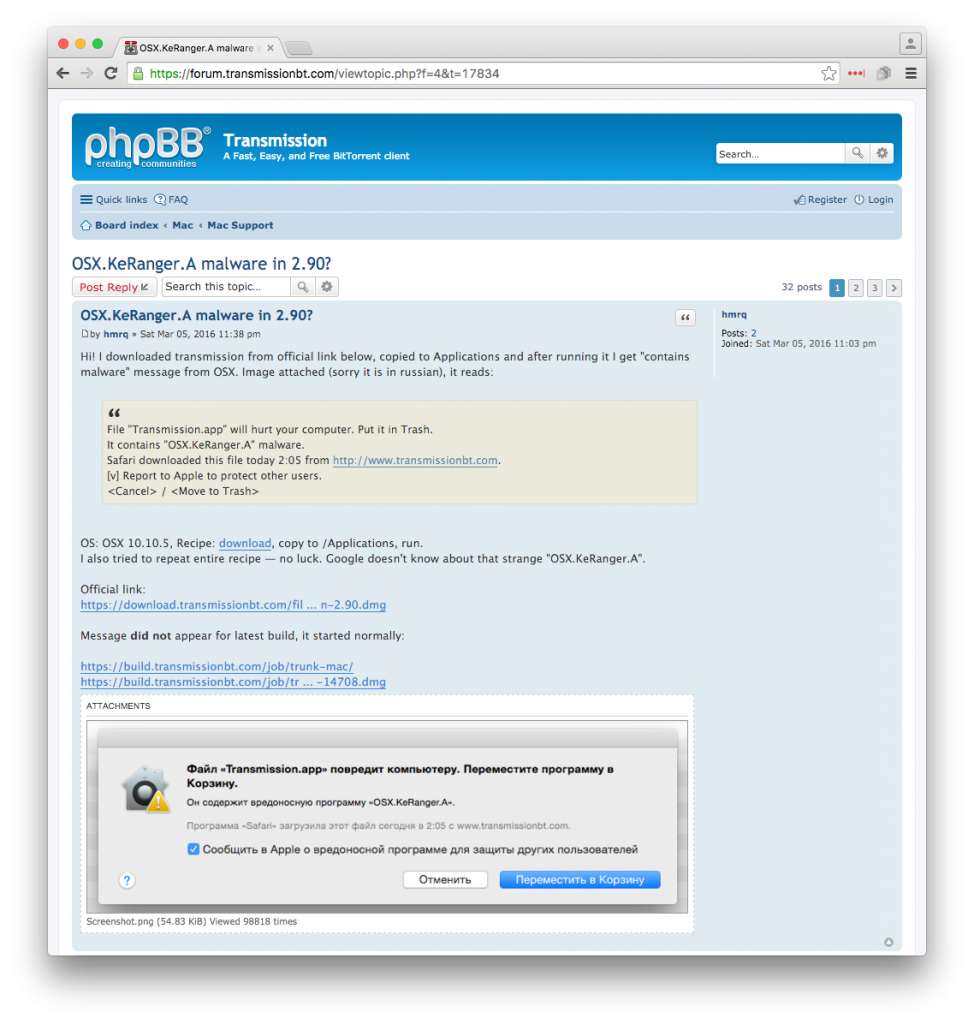
While users began reporting this trojan on Saturday, this trojan was originally discovered on Friday March 4th, just hours after the affected files were posted to Transmissions official site, by researchers at Palo Alto Networks. Upon discovery Friday, the two infected installers for 2.90 were still available on Transmission’s site. However, Palo Alto’s early detection of this trojan likely led to Apple’s prompt signature update to Gatekeeper/XProtect and revocation of the abused certificate on Saturday. Transmission has also since patched their application, removed the infected installers from their site, and posted an alert notice on their front page to inform users of the trojanized version.
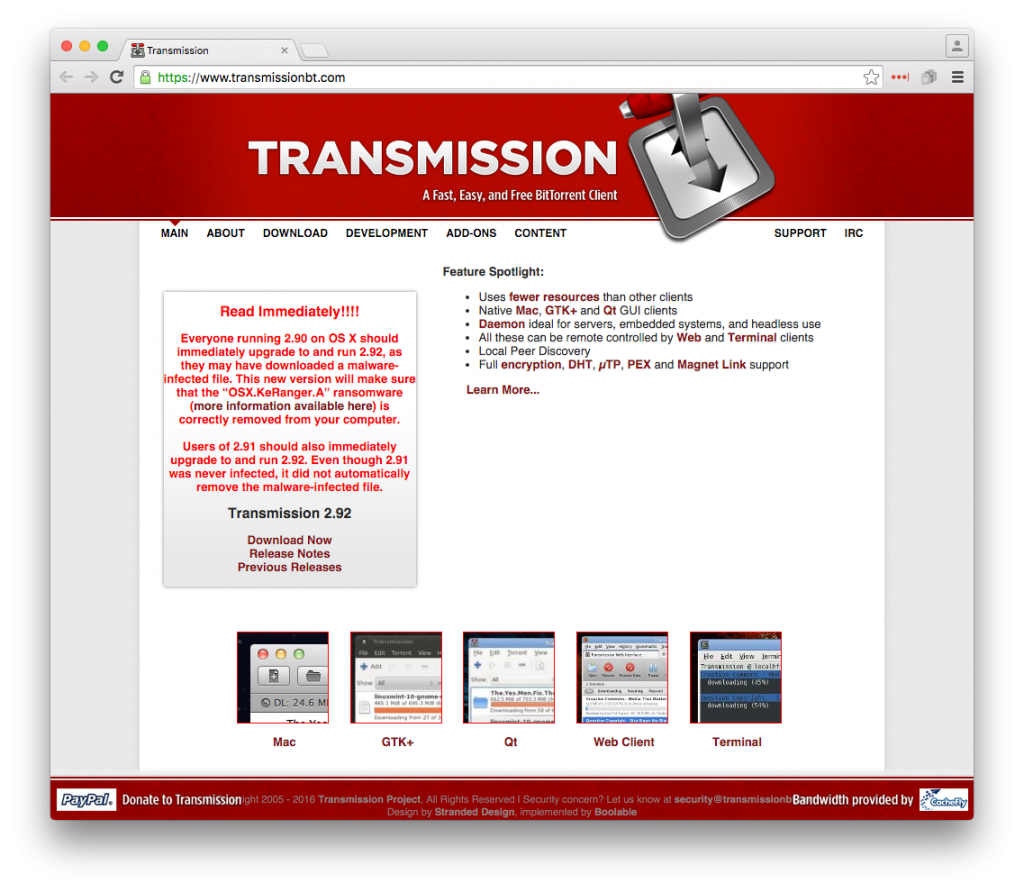
For users who managed to fit in an installation of Transmission between Friday morning and the subsequent updates by Apple, the 72-hour window to prevent the ransomeware would be up ending sometime today, depending on install time. This window is also likely stretching through Tuesday morning for some of the victims who installed the malicious app later such as on Saturday morning. John Clay of Transmission
told ThreatPost
“Our best guess at this point is that approximately than 6,500 infected disk images were downloaded. Of those, our presumption is that many were unable to run the infected file due to Apple quickly revoking the certificate used to sign the binary, as well as updating the XProtect definitions,” Clay said. “We’re waiting on confirmation from Apple on that.” - John Clay
Details of the Ransomeware:
However, Palo Alto Networks researchers were unable to confirm how this infection occurred. They do theorize that it is possible that Transmission’s official website was compromised thus allowing attackers to replace the legitimate files with malicious copies. This type of attack was recently carried out on Linux Mint, a widely popular linux distribution, allowing attackers to embed their trojan into the operating system.
What is known is that attackers signed both compromised installers with a legitimate Apple developer certificate. Both the owner, a Turkish company, and the developer ID signed differ from Transmission’s previous versions but was a legitimate cert recognized by Apple (at the time.)
Once executed, the app copies over and runs an innocuous looking RTF file that is actually an executable itself. This executable then essentially embeds itself and sleeps for 3 days. Some versions of this trojan were also observed communicating with a C2 server every five minutes. This communication sends the Mac’s model name and UUID until the server responds with several lines of encoded data used used for encrypting local files. After it’s 3-day waiting period, the malware will begin encrypting local files associated with 300 fairly common specified file extensions such as .docx and .jpeg.
Palo Alto Networks also noted that it is only aware of one other Mac OS X ransomware trojan, FileCoder, which was discovered by Kaspersky Labs in 2014. More details from Palo Alto Network’s researchers (original discoverers) on this ransomeware can be found in their
New OS X Ransomware KeRanger Infected Transmission BitTorrent Client Installer.


