As the end of the year draws near, we wanted to highlight some of the spam methodology and attacks Cloudmark observed over the past year.
Snowshoe/hailstorm attacks:
Snowshoe spam is a campaign which is distributed across multiple IP addresses within a /24 netblock (256 IP addresses) and migrates through large portions of a /16 (65,536 IP addresses). These campaigns commonly feature hashbuster text within the body of the messages, rotating domains in the call to action, and/or random word combinations in rDNS.
A hailstorm attack is a snowshoe campaign across smaller netblocks (/25 and /27 observed, not always contiguous), mailing over a shorter duration (under one minute, usually within seconds) with simultaneous connections. Typically, spammers engage in snowshoe and hailstorm attacks to evade DNSbls and other IP address and volume based spam filters.
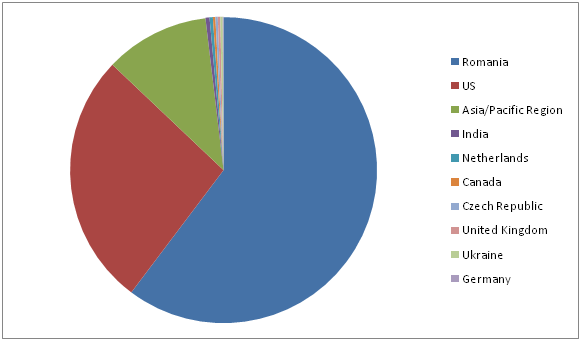
Over the past 30 days, over 60% of the IP addresses sending new snowshoe spam campaigns to the Cloudmark Global Threat Network were located in Romania. IP addresses in the United States were responsible for almost 27% of snowshoe campaigns.
Botnet driven spam:
We have observed a significant amount of spam originating from the Cutwail botnet leading to installers for Zeus/Zbot. Recently,
messages telling recipients to register in the CDC’s H1N1 program have been observed.
URL obfuscation:
Although URL obfuscation is nothing new, we continue to see it used by spammers to evade spam filters and trick the recipient. Some of the obfuscation methods we observed included the use of hex, octal, and HTML numeric and character entity encoding in URLs, the use of extra characters in href tags, and the use of style tags within the domain of the call to action.
Example of HTML numeric entity encoding:
<a href="http://ffq–bz.d107ptsn²01.com/ “>Click here</a>
– is an en dash: –
² is a superscript two: ²
HTML numeric and character entity encoding are decoded and successfully rendered by many mail clients and browsers. In the example above, the domain is ffq–bz.d107ptsn²01.com.
Example of the use of style tags within the domain:
- http://<STYLE>Uqbysa for varykuto Qzufyce jzy</STYLE>fairsha<STYLE>Aziw for suilto Yhaxjnary lygavun</STYLE>pe.com
In a mail client (such as Outlook) or a webmail client, the recipient would only see http://fairshape.com. However, it would be a non-clickable link, so the recipient would need to copy and paste the URL into the web browser.
We have also observed spam containing Google properties (e.g., groups.google.com, docs.google.com, writely.google.com), spaces.live.com, and many other places hosting user-generated content as the call-to-action URL ultimately serving up landing pages advertising online pharmacies. These online pharmacy landing pages are hosted off of the same IP addresses as domains advertised in wavy image spam.

Perfectly innocent websites are being compromised as well and are being used to host spam content (usually redirectors leading to online pharmacy landing sites). These web pages are appearing as the call to action in spam, and unfortunately, due to the high number of insecure websites, the spammers have a dynamic set of hosting resources to burn through.
We also observed an increase in economy related spam. The content varied from debt consolidation services to work at home scams.

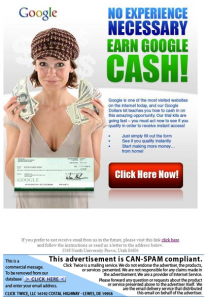
One of the most egregious work at home scams advertised through email, Facebook, and Twitter spam was the Google work at home scam. The messages promoted a free kit for recipients to make money through Google. Unfortunately, recipients were required to provide their credit card information to pay for a small shipping and handling fee. Subsequently, the recipients were charged a substantial recurring monthly fee, and most were unable to reverse or stop the charges. This scam has no legitimate ties to Google. In fact, Google recently filed
suit in US District Court in Utah against Pacific Webworks, Inc. and John Does for violations of trademark, cyberpiracy, and consumer sales practices laws.

