Motherboard reports that researcher
Kevin Beaumont and several security firms have seen the distribution of Dridex and Locky malware stop as of June 1st. These pieces of malware, and several others such as Neverquest2, are spread via Necurs -- what is possibly the world's largest botnet,
as stated by Beaumont.
Currently, the prevailing theory is that this sudden drop is the result of roughly 50 Russian hackers being arrested on the same day. The group in question is charged with using the Lurk trojan to steal over $25 million from various Russian financial institutions.
However, a Russian security group that works closely with law enforcement does not agree. Nikolay Grunin, PR manager for Group-IB told Motherboard:
“We don't see any connection between Necurs Botnet going down and recent arrests in Russia. The arrests of 50 hackers were made in connection to the Lurk group, and that particular group only targeted Russian and Ukrainian banks in their fraudulent activity”
Data collected by Cloudmark supports Group-IBs assessment that these arrests are unrelated. After an initial spike seen on May 25th by both Cloudmark and
other security vendors, Dridex-like and Locky-like message attachments plummeted on the 27th and had nearly disappeared on the 28th. A time-series graph of volumes for several Locky-like indicators in attachments:
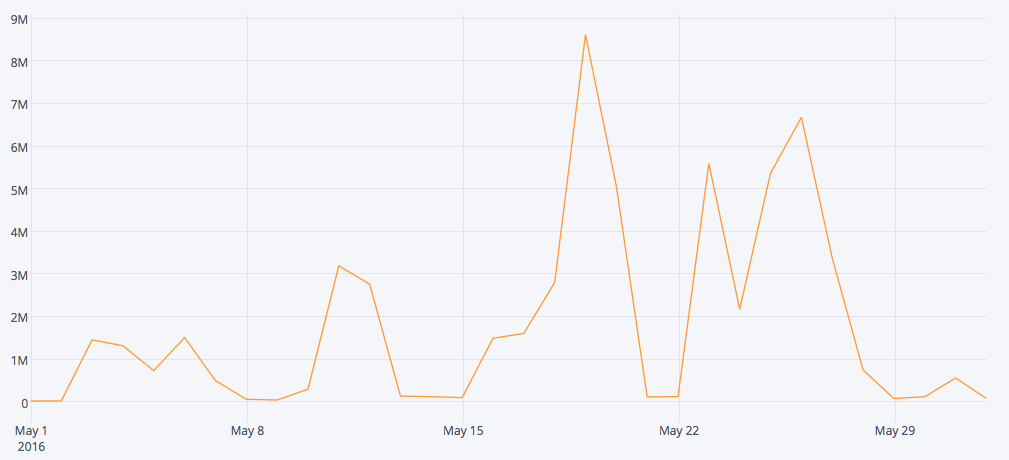
We've
noticed that
in the past many law enforcement takedowns happen
on Friday. Interestingly enough, May 27th, when we first saw the down turn, also happens to be a Friday. This timing would make it entirely possible that this was caused instead by a yet-to-be-announced takedown of the Necurs botnet. It is also worth noting that this early dip may be caused by the weekly cyclic dip in Locky-like malware each weekend as evidenced by the graph above. If a takedown or arrest were to have happened at some point from Saturday through Monday, this compounding, cyclic factor could obfuscate the proper date of the event.
While the cause remains unknown, so too do the repercussions. Removing the botnet would be a definitive win in terms of stopping further infection. However, one form of malware spread by Necurs is the ransomeware known as Locky. This malware infects the victims PC encrypting the users' files, spreading to connected network drives, and demanding that the victim pay a ransom to have their files unlocked. it is unknown if cutting the metaphorical head off of Locky ransomeware will cause currently infected victims to be unable to pay up ransoms to recover their files.
Unfortunately, in 2015, attempts made by several international law agencies that resulted in the arrest of the Dridex botnet's administrator were not successful in stopping the malware permanently. It is entirely possible that we may see the Necurs botnet simply bounce back in the coming weeks.

