We received an SMS pointing to a very odd website via the 7726 spam reporting service earlier and it's sparked off a rather interesting investigation that shows how one rather clumsy SMS spammer annoys victims in the middle of the night.
Imagine the scene: It's 2am. Your phone goes off. Blurry eyed you read the following SMS:
"Currently seeking people to work from home, Free training and no experience necessary, visit www.[redacted].tv"...
If this spammer wanted to annoy "future employees" then he's off to a good start.
We expected some sort of new work-from-home website to blacklist, however this is where this example stops looking quite so vanilla, as the website in question redirects to this site:
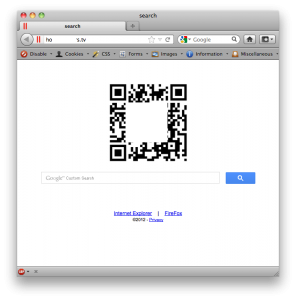
Thats not what any of us expected, right?
The QR code is an image linked to /toolbar/hw.exe (
VirusTotal Link). The decoded QR code itself points to /android/browser.apk. The Internet Explorer text links to /toolbar/install.html and onward to a hw.cab file. The Firefox text links to /toolbar/hw_firefox/install.html and onward to a hw.xpi file. The privacy link funnily enough, does nothing at all. OK, so thats all their bases covered, no matter how recipients choose to interface with the website promoted in the message they're going to get offered some sort of download.
What I find really odd here is the relation between a work-from-home solicitation and installing an application. Even my rather click-happy kids would have alarm bells ringing at this stage.
The IE link leads to a window titled "Softomate web-installer" (see besttoolbars dot net for info). The Android application package (apk file) is signed by Maxthon and would appear to be their
custom browser software, with which anyone can make a self-branded browser app that has a pre-set default homepage. Given that the spammer controls that homepage he or she could of course choose how to monetize it at a later date. I'm fairly sure this is the case, as they have a domain authenticated SSL certificate to which site visitors, who use the search function, are redirected.
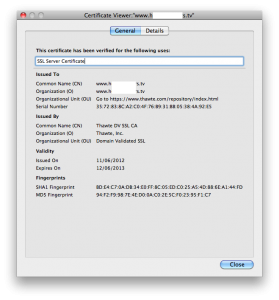
However, since I started looking into this the initial click did briefly change to a recruitment website, so perhaps they just made a mistake? The recruitment site in question looks like a poor facsimile of a company in Leeds, so much so the address is incorrect on some pages, but honestly it's convincing enough.
Looking at the IP address of the site we see a login page for "Internet Dreams" - no adverts, the main hostname of the webserver also shows the same site. However, Googles bottomless cache stops this avenue being a dead end. Here we see another surprise from this guy, a mobile number generator.
[caption id="attachment_1573" align="aligncenter" width="300" caption="Dodgy number generator"]
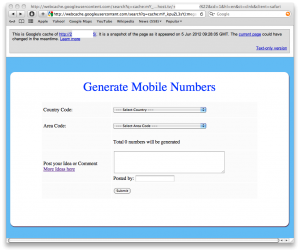
[/caption]
Clearly this isn't a mobile operator. Generating valid mobile numbers en mass is a staple for the SMS spammers. Hosting this sort of thing on the same IP as a spammed recruitment site is highly suspect & proof that the senders and the monetizers are sometimes the same entity. If ever you question how black-hat some of these sites are, one of the sites that was previously parked on the same IP redirects the .com to the same .org domain of a software piracy group called thumperdc, and even if that's a bizarre historic coincidence I find it rather ironic none the less. Moreover they were also involved in a very common PPI SMS spam campaign in the UK :
[caption id="attachment_1606" align="aligncenter" width="554" caption="According to our systems, this campaign used 47 different sending numbers. In the last 7 days this is the most complained about SMS spam campaign in the UK. "]
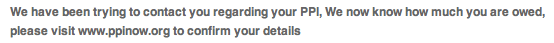
[/caption]
So lets wrap up. SMS Spam was sent and the call to action website was either taken down or incorrectly configured at that time, I believe misconfiguration is more likely as having done a little digging this server appears to have deep roots in the SMS spam world and there are a good number of other sites on the same IP that redirect to the same QR code page. (Ironically including antismsspam dot com - don't visit redacted sites.) and previously, running a mobile number generator, other SMS spammed campaigns. This SMS spammer clearly has his own server and is trying out different types of money-making and this time round they unleashed the spam campaign before the site was online.
Good night & sleep well.
Chris.
[
Thanks to my colleague Vincent who spotted the oddity and brought it to my attention. Kudos to the guys at www.mylookout.com for the app analysis assistance, and finally our first reporter (UK number ending in 89) who diligently reported the spam to 7726 at 2am in the morning!]



