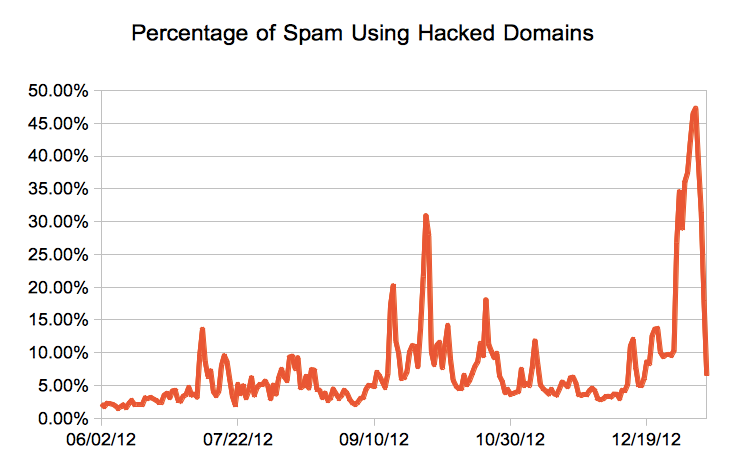
This particular spammer was only uploading a single file to each hacked domain to do his redirection. Others upload multiple files to allow more URLs to be used, and we have seen some domains in which the 404 page not found response has been hacked to redirect to the spammers landing page, so the spammer can send out each spam email with a different URL. So long as they are not part of the original web site, they will redirect if the recipient clicks on them.
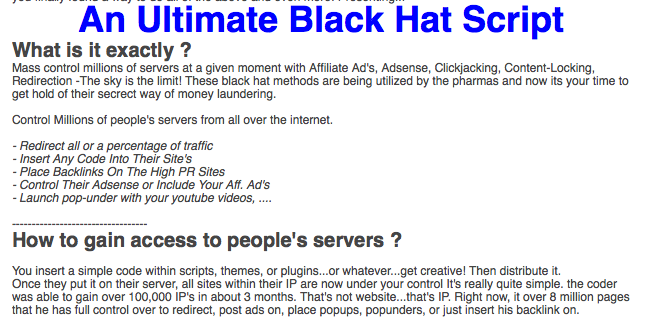
So how are these web sites being hacked? The majority that we see are Wordpress sites, and a significant minority are Joomla. Mostly theses are sites belonging to individuals and small businesses who may have set up a site a few years ago and make very few updates, to either content or software. However, older versions of both Wordpress and Joomla have some well documented vulnerabilities, so if you don't keep your site up to date you may well be a target.
Even if you do always have the latest software in place, you can still be hacked if you install the wrong theme or plug in. Just recently in the black hat underworld, malicious code was offered for sale that allows the user to add a trojan to installable Wordpress modules...
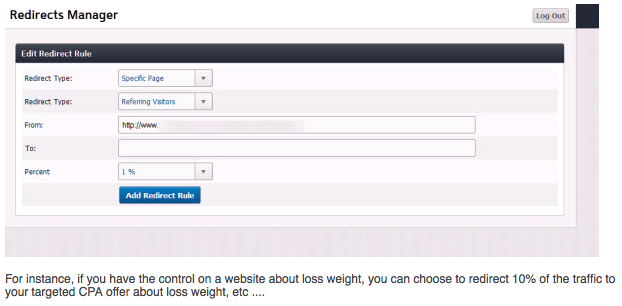
Once the user installs the innocent looking plug in, the hacker can then upload and execute arbitrary code or even use the built in redirect manager.
That was offered for sale for just $100, but sorry, it's all sold out now.
To prevent the embarrassment of having your web site redirect to a porn site in Russia, keep your web site software up to date, be careful what themes and plug ins you install, and keep an eye on your server log for any traffic to pages you don't recognize.