It's been a hot year for messaging security. In our
2014 Annual Security Threat Report we take a look at, among many other topics, findings of DNS resource exhaustion/water boarding at a major ISP, a deeper look at the highest volume spam campaign to reach Apple iMessage users to date, and delve into the a chemical analysis of samples from several of those fake pharmacies always trying to sell you Viagra®
Viagra® advertisements in email have become pervasive enough that their comical existence are the butt of many jokes. But, how serious are these offers for cheap prescription medications? This year, we decided to investigate several of these online pharmacies. Cloudmark went about attaining samples from several online pharmacies using spam emails to advertise their wares.

We chose the generic Viagra® sold by spammers and commissioned a chemical analysis of the samples. Beyond a surprising quality of customer service, the samples contained the same active ingredient as the real drug. However, lab results suggest that some impurities such as trace amounts of acetaminophen and a significant proportion of diclofenac snuck in. Diclofenac is a pain killer which in rare cases can actually
cause erectile dysfunction. This along with being distributed without prescriptions, dosage advice, or health warnings is reason for concern.
Cloudmark took a similar approach this year while researching an emerging spam campaign targeting Apple iMessage.
Over the past year, Apple's iMessage has come to be plagued by unprecedented levels of spam from a campaign offering counterfeit designer goods at discount prices. This iMessage spam reached a peak over the summer, accounting for 43 percent of all reported mobile spam in the United States for the month of June.
For this set of spam, we again ordered several samples of merchandise from the vendors. In doing so, we ran into our first big surprise. It turns out customers actually receive the item! Naturally, these poorly done replicas of real products are far inferior in quality. This psudo-scam still, however, remains an infringement on the brands used to sell the knock-offs. More details on the origins, methods, and legal chase surrounding this campaign can be found in our
2014 Annual Security Threat Report.
While diagnosing the DNS infrastructure of a major ISP, Cloudmark uncovered the use of an emerging form of DNS attack known as a resource exhaustion or water-torture attack. This attack uses maliciously crafted DNS lookup requests that are impossible to resolve. Doing this affected the ISP's DNS infrastructure in two places:
- Authoritative servers were swamped with a large volume of requests.
- Intermediate resolvers forced to wait on the end target’s authoritative name server experienced delays and timeouts.
These delays and timeouts consume network, CPU, and storage resources at the intermediate resolver – giving rise to the attack's name.
This is carried by identifying a remote target and a domain name owned by that target. In this case, that domain was 500sf.com. Then, a botnet of compromised machines and open resolvers are used to flood the target with malicious lookup requests for random, unique, and non-existent subdomains of that domain name. Below is a 30 minute sample of an attack used against a target ISP:
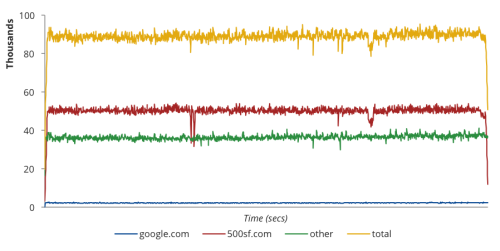
Volume of Outstanding Requests, Sampled on May 29, 2014
For more information about this attack and other abuses of DNS infrastructure such as DDoS attacks using DNS amplification, malicious DNS tunneling, and data exfiltration via DNS please see Cloudmark's
2014 Annual Security Threat Report.



