Key takeaways
- Attackers are now leveraging video attachments in multimedia messages (MMS) in mobile to promote Bitcoin scams, marking an evolution from static images.
- A reported video message came in a lightweight 14KB.3gp file—a unique approach for convincing victims to click links and engage with scammers.
- Recipients are lured to WhatsApp groups, where scammers use high-pressure tactics to extract money or personal information.
- MMS abuse is expected to grow with increasingly deceptive multimedia content to target unsuspecting individuals.
Overview
The rise of image-based Bitcoin scams has been a growing concern for defenders in the mobile space. Attackers use eye-catching, fraudulent images to lure victims into schemes promising extraordinary financial returns. Now, a new and troubling trend is emerging: video-based abuse (VidSpam), where attackers are leveraging small video file attachments to further enhance their deception tactics.
Bitcoin image abuse
No sooner had we sounded the alarm about image abuse becoming a widespread attack technique targeting mobile device users, through image message spam, than Proofpoint researchers noticed the emergence of video message abuse, adding another layer to scammers' tactics.
Bitcoin scams via MMS images have become commonplace in unwanted message reports. These scams often feature images of successful-looking individuals, fake awards, and promises of extraordinary daily profits. Their sole goal: to convince recipients to part with their hard-earned money.

Example of Bitcoin image spam.
Scammers take advantage of the belief that people have made money in cryptocurrency markets, and their scams leave victims financially drained.
A surprising development: video in MMS
In mid-December 2024, Proofpoint researchers identified an MMS based message with a Content-Type: a video message header and a .3gp file attachment was reported to a carrier and Proofpoint’s Mobile Abuse Visibility solution as unwanted. This small video-based attachment is received on mobile devices and contains a “play” button that allows recipients to easily start the video.
Clicking the button results in a brief, 2-second video that merely displays the static image shown below. Unlike most video files, there is no movement or animation in this video—it simply presents the graphic as if it were a still image.
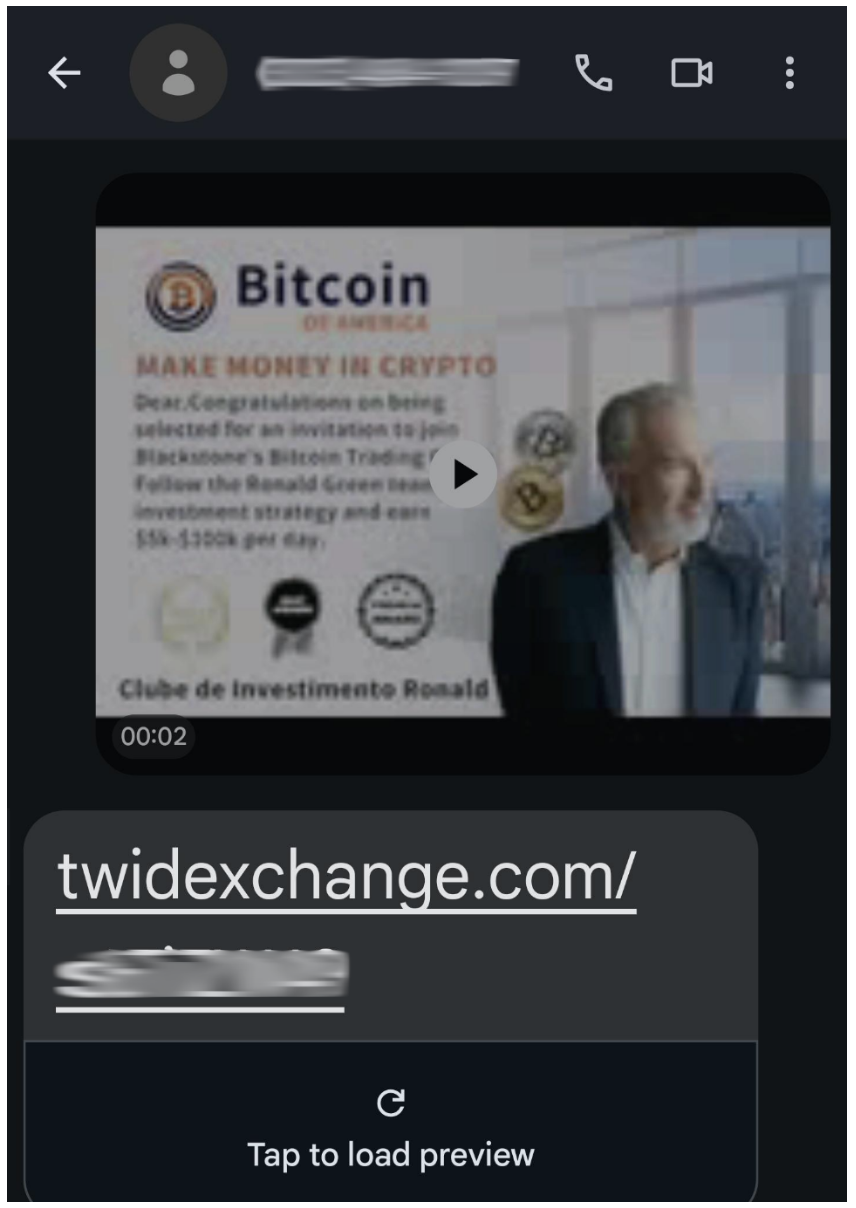
.3gp video as shown in messaging app.
What is a .3gp file you ask?
A .3gp file is a multimedia container format designed for 3G networks and optimized for small file sizes and efficient streaming on mobile devices. The small size makes these files accessible on devices with limited storage and on slower networks. This combination of size and low resource use makes the format ideal for mobile devices on both low-data environments and modern 4G/5G networks.
The video attachment in this example was crafted to be a mere 14.1KB, an unusually small size for a video file. The message body only contained an embedded link directing users to the attacker-controlled discussion forum. This evolution is surprising and highlights how attackers adapt their methods to evade detection of traditional content filtering more commonly attuned to scanning text and image-based messages.
The small video size results in a video with very low resolution and poor quality. Its purpose is not necessarily to entice users visually, rather, it’s designed to add credibility and increase the likelihood that the recipient engages with embedded content or through a message response.
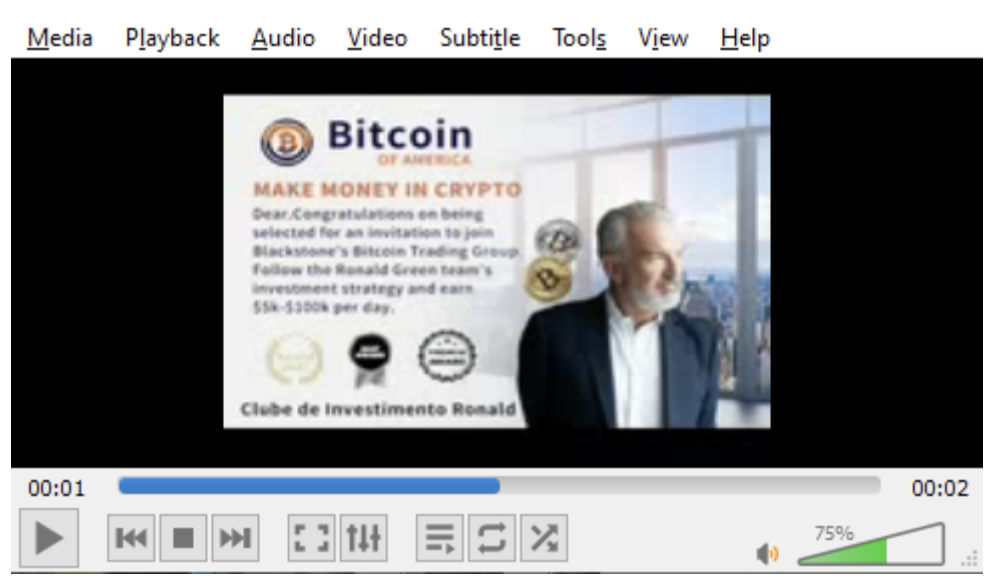
VidSpam Bitcoin message.
How the scam works
The MMS message contains both a message body and video attachment. The message body typically contains nothing more than a link to a URL redirection service, which directs the user to an attacker-controlled webpage. The video attachment is intended to add credibility, while the body urges recipients to click the link and join a WhatsApp investment group. Once inside, scammers assess the victim’s credulity before deploying high-pressure tactics and crypto related investment opportunities which encompass their fraudulent schemes.

WhatsApp investment group invitation (https://chat.whatsapp.com/L8D8CtEIBI28WWqsVWEZsA).
This tactic is like job-seeking scams, where victims are convinced to write fake reviews or complete fake tasks in exchange for payments that never materialize. Fellow Proofpoint researchers have recently documented a similar scam in their post: Pig Butchers Join the Gig Economy: Cryptocurrency Scammers Target Job Seekers.
Why this is effective
Mobile devices are an attractive target for attackers because they are highly personal, user-friendly, and constantly available. As we have previously shared, 99% of received mobile messages are opened, and 90% are read within just 3 minutes of receipt. Additionally, the number of people who send and receive text messages is expected to increase to 5.9 billion by 2025, representing the massive global audience that attackers can exploit.
The bigger picture
These scams are part of a broader trend of mobile messaging abuse that has generated billions of dollars for attackers. The 2023 FBI Cryptocurrency Fraud Report shows $5.6 billion dollars lost to Crypto-Investment scams, a 45% increase over 2022. The 2024 FBI IC3 report, due out in early 2025, will likely show yet another increase to this highly successful scam.
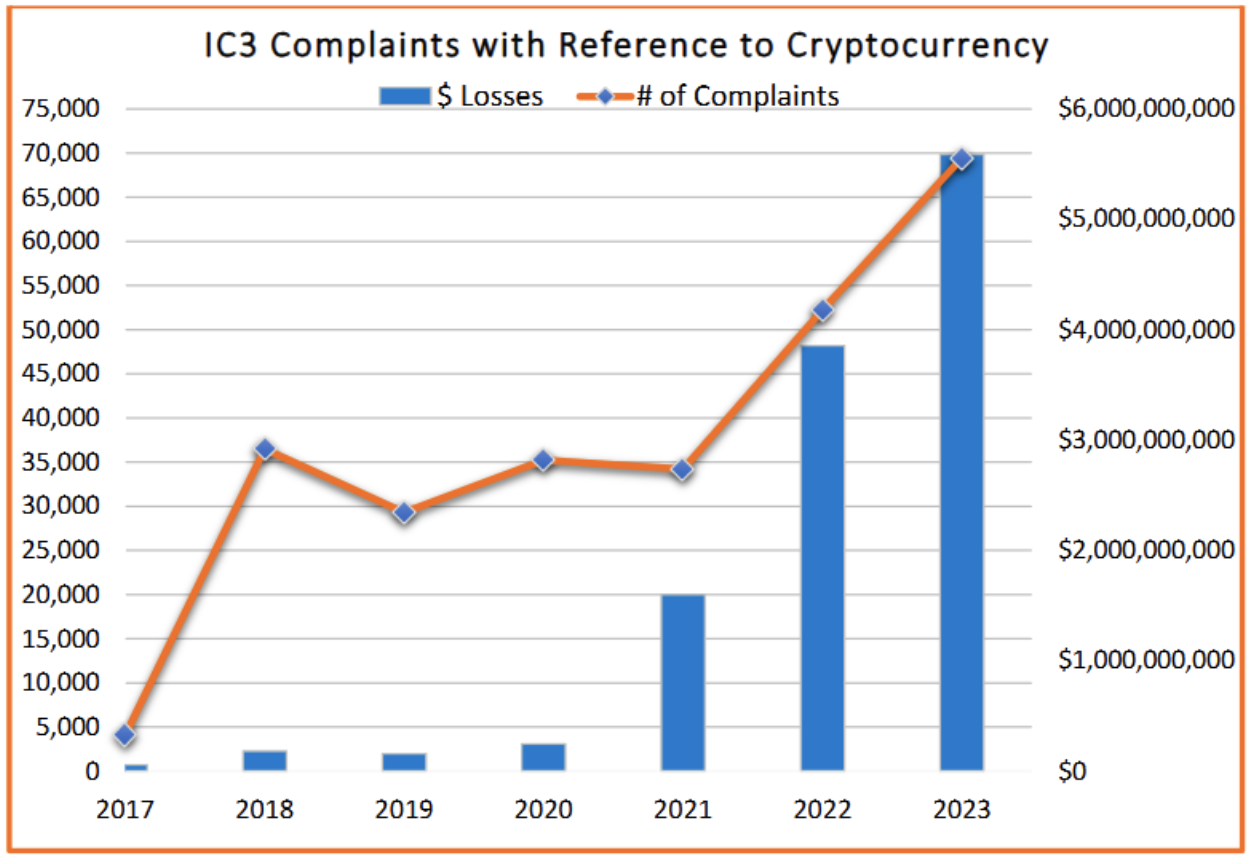
FBI cryptocurrency fraud report.
What’s more concerning is how scammers are using increasingly sophisticated, likely, AI-generated images and multimedia, making it harder for even scam-adverse individuals to discern legitimate messages from fraudulent ones. Research conducted by Price Waterhouse Cooper (PWC) on the impact of Artificial Intelligence on Fraud and Scams demonstrates how generative text and image content can be used to amplify fraudsters’ potential reach by enabling content at greater speed, scale, and sophistication.
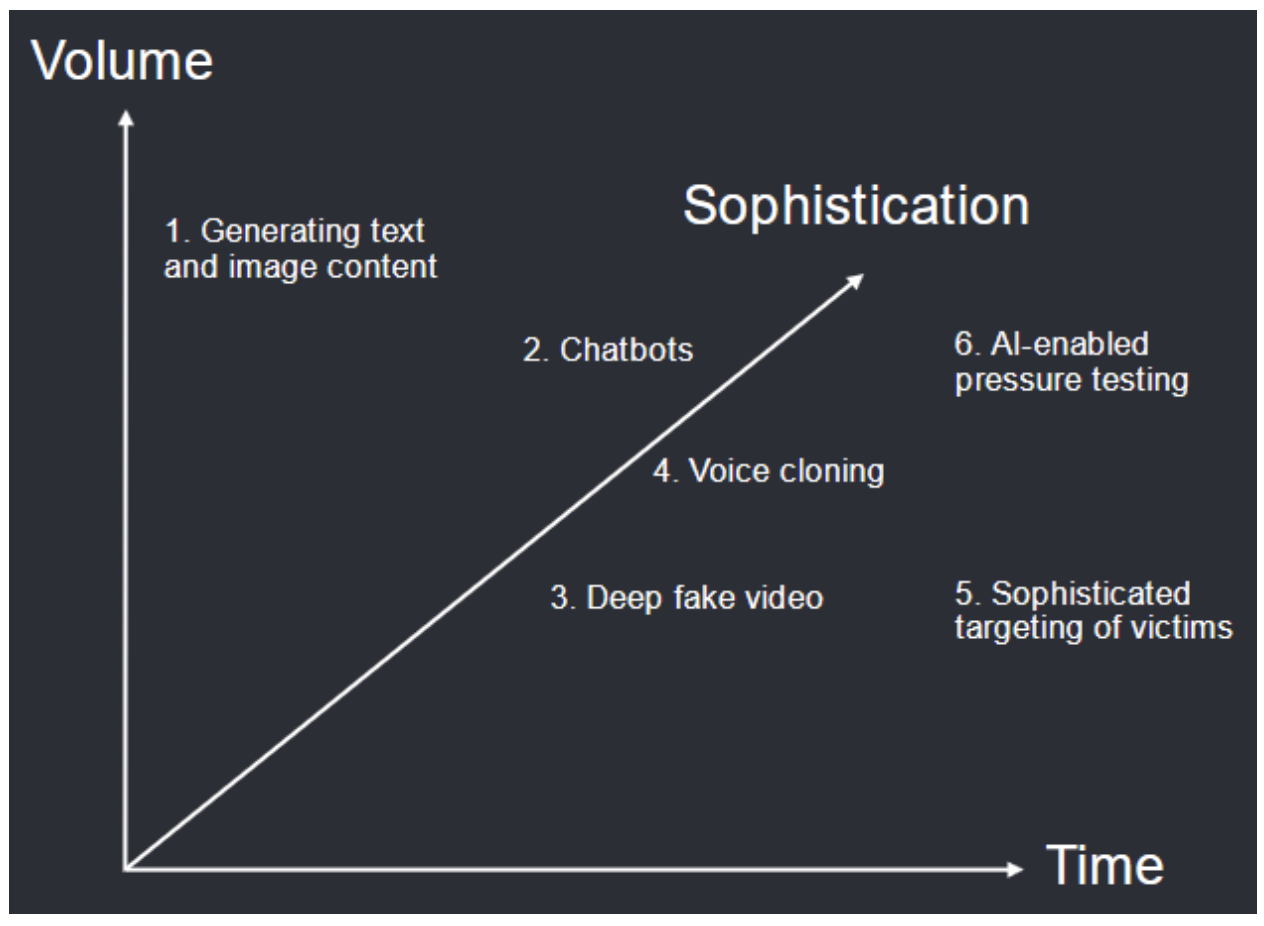
PWC: Impact of artificial Intelligence on fraud and scams.
Conclusion
As scammers refine their tactics, defenders and consumers must remain vigilant and adapt to emerging attack chains. While video-based abuse may not signal a new era of deception, it represents an evolution in the tools attackers use to exploit victims. Collaboration across the industry is essential to staying one step ahead of these ever-changing threats.
MMS represents an uphill battle as abuse matures and introduces new challenges like video-based scams (VidSpam). Here are some best practices to stay protected:
- Be skeptical of unsolicited offers, especially those promising unrealistic financial returns.
- Avoid clicking on links or downloading attachments from unknown sources.
- Never send money or share personal information with someone you don’t trust, especially over mobile messaging platforms.
- Report suspicious messages to your mobile carrier and the Mobile Abuse Visibility Solution run by Proofpoint. To do this, make use of the built-in iOS and Android reporting features by clicking “Report Junk” on iOS or “Report Spam” on Android devices.
