With the New Year, it appears SMS scammers in the U.S. have taken a renewed interest in bank and account phishing mobile users. In January alone, more than half of all SMS spam reported via the
GSMA Spam Reporting Service within the US were phishing attempts. From targeting prepaid debit cards for Child Support Recipients to swiping recipients’ mobile accounts out from under their own feet, the relative amount of phishing reports in the U.S. jumped 68% from December to January.
Top 5 Types of U.S. SMS Spam, January 2013
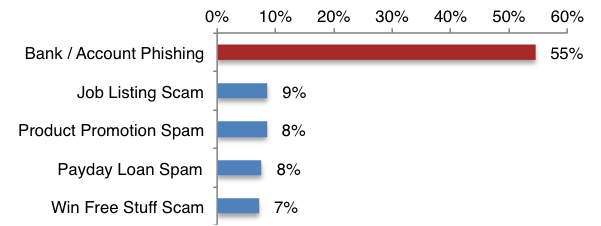
Of these phishing messages, the single most common type of target was prepaid debit cards. Nearly 54 percent of all phishing reports last month looked for prepaid debit cards. It’s likely that attackers favor these prepaid debits due to a relatively lower risk. Many of these cards contain very little fraud protection or prevention and can often be used directly from many ATMs to withdraw cash – an appetizing combination for thieves. Prepaid AchieveCards are a prime example. Targeted by 90 percent of prepaid debit card phishing attempts last month, these cards were favored a staggering amount. Given Achieve’s settlement with the FDIC for
shady business practices last year, attackers likely see this card specifically as easy pickings.
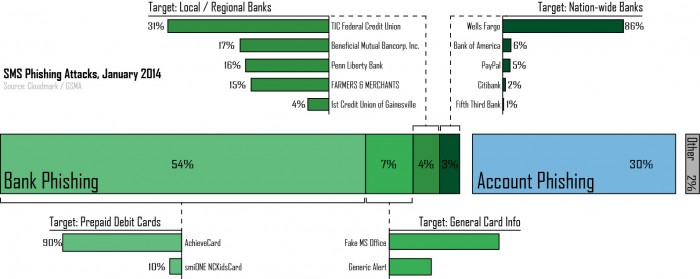
Child support recipients in North Carolina receiving their benefits via a smiONE prepaid debit card should also be wary. Just shy of 10 percent of prepaid debit card phishing messages knowingly targeted the NCKIDSCARD using child support for the hook:
FWD: C h i l d S u p p o r t D e b i t C a r d [4 8 7 6 5 5 X X] I s s u e. C a l l :[REDACTED]
FWD: ([smiONE]) ChildSupport[478655XX] NCKidsCardAccountIssue Call:[REDACTED]
After prepaid debit cards, the second most common phishing target was mobile accounts. Thirty percent of all phishing attempts sought to hijack the mobile subscriber’s account credentials. This was accomplished using messages and mobile sites custom-tailored with branding from the mobile operator associated with each recipient. Those messages using custom-branded SMS showed a high degree of accuracy with regards to delivering correctly branded messages to number using the intended major carrier. Attackers were just short of 100 percent accurate with their SMS message’s carrier branding, suggesting that the attack is using a list of known numbers and associated carriers or some other means outside of the normal blasting of random numbers. More details on these custom-branded mobile sites can be found in another of our
recent blogs.
In contrast to prepaid debit card phishing, nation-wide and international banks have been targeted less in recent months. Only 3 perecent of January’s phishing attacks went after these major institutions. Of these, Wells Fargo was a clear favorite with associated campaigns contributing 86 percent of messages targeting nation-wide & international banks.
At least 15 local and regional banks and credit unions were targeted in concentrated attacks last month. Recently, a series of short-burst phishing attempts have been made against account holders with these local entities which all follow the same trend. For about a day, attackers blast out phishing messages disguised as alerts from a local credit union or bank to a few, very specific, area codes associated with the relevant bank. Then, they disappear, off to target a new area and bank.
One interesting niche attack actually used Microsoft Office as its hook. About five percent of phishing attacks last month offered Microsoft Office at discounts of up to 75% for a limited time (usually 30 minutes.) Victims who followed the link were taken to a phishing site with a fake countdown of the time remaining on the deal. Anyone willing to willing to pay for the obviously fake offer has their credentials promptly sent off to the attacker and are met with the fake promise of a pending download link that will soon be delivered to your email address.
However, These phishing attempts are easily thwarted with a few key habits:
1. Never call any phone number provided in an unsolicited SMS.
2. Never click or follow any link provided in an unsolicited SMS.
3. Never reply to an unsolicited SMS.
4. If concerned about an account, contact your bank or provider of the service directly;
Debit and credit card providers are best reached by calling the phone listed on the back of your individual card.
5. Forward any suspicious text messages to the shortcode SPAM (7726).
Edit 03/03/14: 78% jump from December to January cited in the first paragraph was corrected to 68%.


