Global SMiShing is increasing at an alarming pace and Proofpoint analysis shows mobile complaints increased a staggering 790% from the end of Q1 2020 through the end of Q1 2021. By utilizing data derived from the largest, most robust mobile and email messaging threat matrix in existence, the Cloudmark Global Threat Network, Cloudmark threat analysts have identified a unique multi-modal bitcoin attack utilizing a socially engineered combination of mobile and email messaging to give the target victim the illusion and impression of legitimacy. As Bitcoin’s price skyrockets and it becomes more adopted, yet difficult to trace and monitor, scammers are increasingly using it as currency in their complex attacks.
A multimodal attack is an attack that is propagated through multiple communication channels. The example shown here is a five-stage attack using the mobile and email channels. Stage 1 begins with an unsolicited SMS message that contains a link to an authentic-looking job application form. With Covid-19 causing financial hardships, some people are willing to try a new side job to make up for lost income. The message describes the job of evaluating and testing newly installed Bitcoin ATM machines for hundreds of dollars. At this stage the scammer has a real phone number for the target and potential victim.
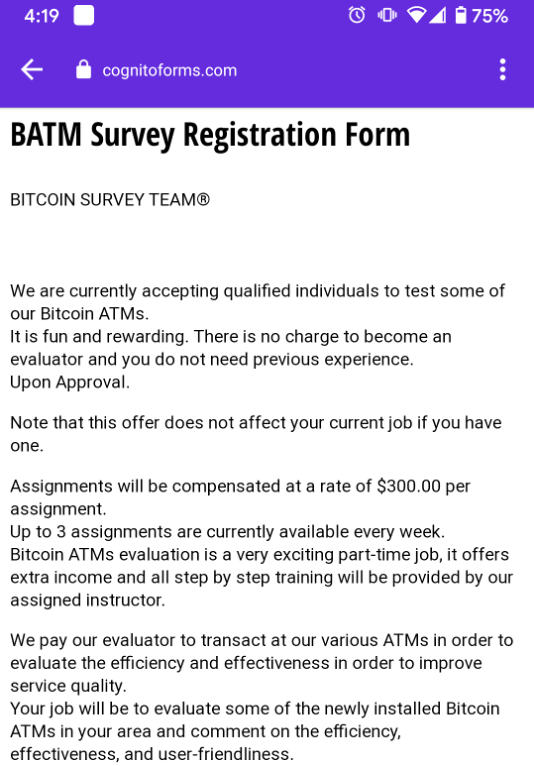
Once the job application form has been submitted, and the second phase commences, the scammer will reach back out via a text message to confirm the email address. At this point, the scammer has the victim’s phone number, name, and email address.

In the third stage, the scammer begins communication over email and provides more details about the testing and evaluating that are required at the Bitcoin ATM. The instructions suggest that there will be Bitcoin wiring completed which scammers refer to as purchases in order to test the entire process of using the Bitcoin ATM.

During fourth stage, the scammer is persistent with communications from the scammer continuing over email and mobile channels. After the ‘job’ has been accepted and before receiving the first Bitcoin ATM assignment, the scammer will ask for the victim’s bank account information and for confirmation of the victim’s identification. Identification verification is completed through the legitimate third-party site id.me, which is used by federal and state agencies.
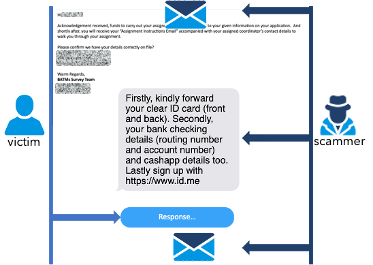
As part of the fifth stage, and after the required verified information has been provided to the scammer, the scammer will send another email that indicates how the money will be deposited into a bank account. The scammer provides a QR code that is the scammers’ Bitcoin wallet address and will provide an instruction to use some of the money deposited into the bank account to purchase Bitcoin at the Bitcoin ATM and send it to the wallet provided. This last stage is a ruse as the money provided by the scammer is via a fraudulent check that will not be settled in the victim’s bank account. At this point the victim would be sending their own money and the scammer would have succeeded in gaining money in addition to a wealth of personal information.

This attack is significant because consumers maintain high levels of trust in the mobile channel today and we need to ensure that this trust is not eroded. By using multiple communication channels, scams appear more authentic to targets, lowering the target’s skepticism of the exchange, and making themselves more vulnerable. Also, by developing multi-modal attacks scammers attempt to evade pattern and language recognition in detection systems. In the example discussed, the scammer cultivated a regular and persistent communication with the victim where the ultimate goal was to collect personal information and money. Recent surveys have shown that nearly 70% of adults are unfamiliar with SMiShing – phishing over the mobile channel - and it is therefore more important than ever that consumers receive threat intelligence regarding these attacks. In order to protect yourself from being scammed, it is best not to reply to anything that seems suspicious or asks for personal information. Instead report the message as spam via the Report Spam button on Android devices or forwarding the message to #7726 on iOS and other devices.
