Up noticeably this month, a new form of broader bank phishing attacks seems to be targeting various parts of the U.S. including Las Vegas where 63 percent of all reported SMS spam turns out to be bank phishing. The trend continued during the finals days of August as an average 46 percent of all reported SMS messages each day in the U.S. were bank and account phishing attempts.
At the turn of the year, we saw a long-winded SMS bank phishing campaign targeting singular area codes, one at a time, coupled with fakes warnings from local and regional credit unions and banks. This type of attack has since tapered off and gone quiet in recent months but is now being replaced with a more widespread attack against customers of several major banks.
This category of unsolicited SMS messages were the third most common form of U.S. SMS attack during all of August. Similarly, the category came in third place during July as well with 14 percent of the U.S. volume that month.
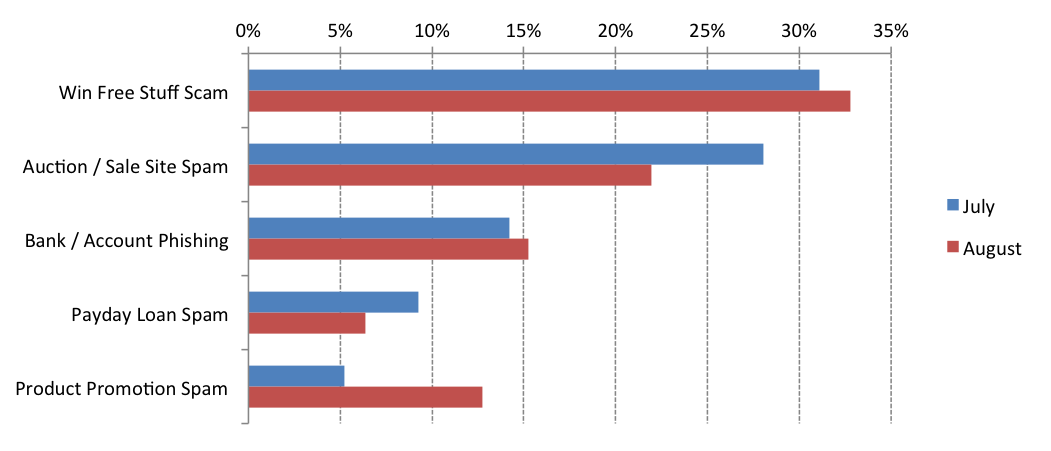
Previously this year we saw a round of highly targeted bank phishing attempts on specific area codes using only regional financial institutions. These attackers have spread their net much wider this time using larger brands such as Chase, Bank of America, and Wells Fargo. Curiously though, these campaigns are, yet again, seemingly honed in predetermined locations. We would expect to see a set of messages blasting out to as many subscribers as possible to hit mostly largely populated area: New York City, Los Angeles, etc. These are instead popping up in smaller U.S. cities such as Denver and Las Vegas:
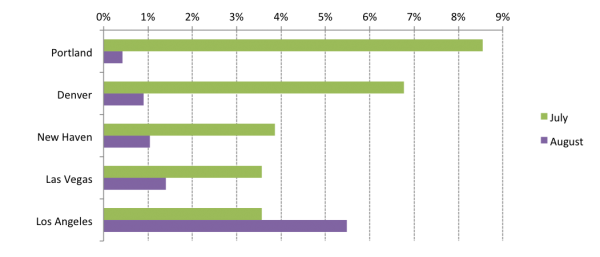
It’s interesting to see lower population cities top the list for most impacted cities. We would expect to see a set of messages blasting out to as many subscribers as possible to hit mostly largely populated areas. Instead, these messages are popping up in smaller U.S. cities such as Denver and Las Vegas. These locations are small enough that other forms of spam have proportionally lower volume in these area codes due to there being less subscribers. Yet, in Las Vegas for instance, it looks like more than just casinos might be siphoning money from residents’ bank accounts. Bank and account phishing attempts make up 63 percent of all reported SMS in the city. For comparison, scams hooking recipients with free prizes are more than double the volume of bank and account phishing attempts in most of the U.S.
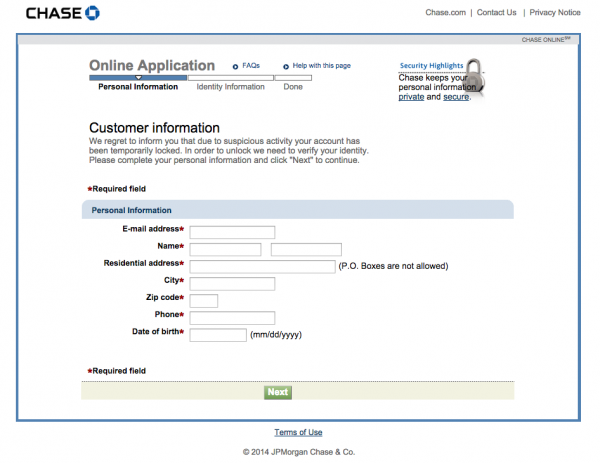
These recent attempts have come in two main varieties. The first, slightly more sophisticated-looking attempt, purloins the website brand images of Chase, Bank of America, and Wells Fargo while hosting them on poorly disguised, disposable domains such as “id0201-bankofamerica.com.” The landing page for Chase begins by asking for a bit of sensitive information:
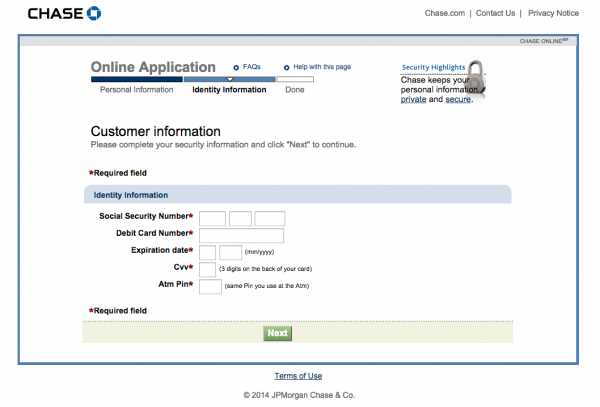
And then quickly escalates to requiring more sensitive information to supposedly recover one’s account:
Upon further investigation, we noticed that many of these dispensable domains shared a common Indonesian IP address belonging to an ISP in the region. This suggests, but is not conclusive, that the perpetrators have a possible connection to or live in the country.
The second, less sophisticated, attack sets up shop on innocent, hacked domains. On these compromised domains, attackers have put up a rudimentary series of questions and forms in the hope of scrapping valuable personal data. One set of questions they attempt is a blanket set of challenge questions:
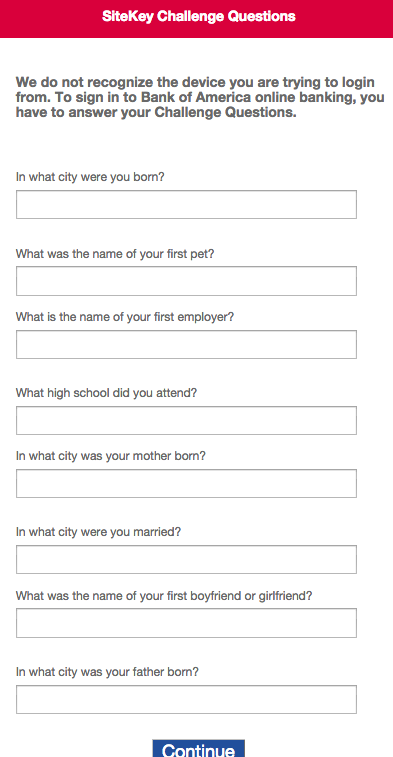
Answer to these types of messages are fairly potent. Most individuals are less likely to create unique answers to these types of questions across multiple sites, and proper answers usually allow an attacker to usurp an account from its holder completely. More and more people are beginning to at least permutate their passwords between websites so checking compromised passwords against other sites such as banks may not be as useful. Challenge questions however, are far less unique on average.
Yet another attack also played a role in placing Los Angeles and Portland on the map: Apple ID phishing.
We’ve seen these messages a number of times over the past several months with a majority of the Apple account phishing attempts, 30 and 16 percent respectively, hitting Portland and Los Angeles. While these phishing attempts in Hollywood’s backyard may not be directly responsible for the privacy-destroying
photo leaks recently surfacing, they highlight the very real implications that such phishing attacks can have on someone.
Apple’s response::
“… we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet.”
Whether challenge questions, simple passwords, or even the login ID to your account, always be suspicious of unsolicited messages asking for your information. Should you ever need to contact your bank regarding a potential issue, always use the contact information provided on the credit or debit card issued to you. Alternatively, if you need to contact the provider of sensitive accounts, manually navigating to the official website also provides reliable methods for contacting your provider rather than reply directly messages or clicking possibly malicious links.









