Congratulations! You have been randomly selected to receive an account Credit, please visit http://[redacted]/[redacted]
Hurray! You are one lucky customer getting a 5% discount on your next month balance, please login: http://ow.ly/[redacted]
Excellent! You are one lucky customer getting a 35% discount on your next month balance, please visit: http://ow.ly/[redacted]
Hurray! You are one graceful customer getting a 40USD discount on your next month invoice, please visit: http://ow.ly/[redacted]
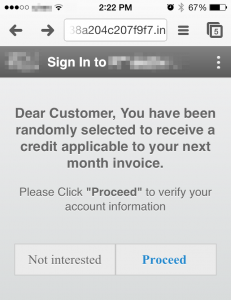
 Mobile Phishing Sign In Page - Designed to steal the subscribers User ID, Password and Last 4 digits of their Social Security Number.[/caption]
But if you were to follow this link with a desktop browser, you'd get a "Page Not Found" error - a dead link.
Well, only mostly dead: The phishers are detecting whether the browser is mobile or desktop; mobile browsers get malicious content, and other browsers get an HTTP 404 status code. It seems likely that the phishers are returning the 404 to try to deceive anti-abuse services: if the link is dead, then there's nothing for the anti-abuse service to analyze, and hopefully the link will be classified as innocuous.
URL shortener abuse isn't new, and shortener services have a responsibility to prevent that abuse. Many services accept abuse reports and take proactive actions such as checking URL contents. For example, bit.ly fetches the original URL it has shortened (and even checks robots.txt, honoring a site's expressed policy on being indexed) - exactly the kind of proactive checking the phishers are hoping to deceive.
We've seen older samples of this attack abusing bit.do. However, bit.do has defanged the short URLs, and they now redirect to http://phish-education.apwg.org/ instead of the malicious site.
But recent samples show that the phishers have moved on to ow.ly, which doesn't seem even to check the original URL. Nor does ow.ly have an obvious way to report abuse - it took some searching on Google and in forums to discover they suggest contacting abuse@hootsuite.com.
Twilio's had problems with accusations of spamming before (see the class action complaint here). Despite that, they don't have an obvious way to report abuse - again, we had to do a Google search to find a web form here.
URL shortening services like ow.ly and advanced telecommunications services like Twilio offer real value to individuals and organizations, lowering the barriers to communication and connection - usually a great thing. But they're also open to abuse, and they need to recognize their part in helping to prevent it.
Email showed how any messaging system that becomes popular becomes a target for abuse. Mobile is growing, and for many users and businesses, it's the next step in messaging - and as we see in this attack, it's the next step for the phishers as well.
Update: Twilio contacted Cloudmark after reading this post and let us know that they have been working to resolve this issue, and that they take abuses like this seriously.
We are now in discussions with Twilio around how we can work together to further mitigate current and future issues of abuse.
Mobile Phishing Sign In Page - Designed to steal the subscribers User ID, Password and Last 4 digits of their Social Security Number.[/caption]
But if you were to follow this link with a desktop browser, you'd get a "Page Not Found" error - a dead link.
Well, only mostly dead: The phishers are detecting whether the browser is mobile or desktop; mobile browsers get malicious content, and other browsers get an HTTP 404 status code. It seems likely that the phishers are returning the 404 to try to deceive anti-abuse services: if the link is dead, then there's nothing for the anti-abuse service to analyze, and hopefully the link will be classified as innocuous.
URL shortener abuse isn't new, and shortener services have a responsibility to prevent that abuse. Many services accept abuse reports and take proactive actions such as checking URL contents. For example, bit.ly fetches the original URL it has shortened (and even checks robots.txt, honoring a site's expressed policy on being indexed) - exactly the kind of proactive checking the phishers are hoping to deceive.
We've seen older samples of this attack abusing bit.do. However, bit.do has defanged the short URLs, and they now redirect to http://phish-education.apwg.org/ instead of the malicious site.
But recent samples show that the phishers have moved on to ow.ly, which doesn't seem even to check the original URL. Nor does ow.ly have an obvious way to report abuse - it took some searching on Google and in forums to discover they suggest contacting abuse@hootsuite.com.
Twilio's had problems with accusations of spamming before (see the class action complaint here). Despite that, they don't have an obvious way to report abuse - again, we had to do a Google search to find a web form here.
URL shortening services like ow.ly and advanced telecommunications services like Twilio offer real value to individuals and organizations, lowering the barriers to communication and connection - usually a great thing. But they're also open to abuse, and they need to recognize their part in helping to prevent it.
Email showed how any messaging system that becomes popular becomes a target for abuse. Mobile is growing, and for many users and businesses, it's the next step in messaging - and as we see in this attack, it's the next step for the phishers as well.
Update: Twilio contacted Cloudmark after reading this post and let us know that they have been working to resolve this issue, and that they take abuses like this seriously.
We are now in discussions with Twilio around how we can work together to further mitigate current and future issues of abuse.
