For a long time we've been seeing spammers systematically compromising other people's web sites to use URLs on them to redirect to the spammers landing page. This allows them to have a far greater range of call to action URLs in email spam. A recent attacker is not only using hacked web sites as redirectors, he is also putting the entire landing page on a different hacked domain. The landing page with the banner shown below, for example, was hosted in a hidden page on the web site of a school, a maker of costumes for children, a law enforcement officer, a therapist, several lawyers, several churches, and many others. The banner is the start of many screens full of hard core pornographic images, all hosted on the victims' web sites.

In the past we have seen spammers exploiting
vulnerabilities in WordPress and Joomla to allow web sites to be attacked. At the moment there are
reports of a large scale attack against WordPress sites using a brute force method of trying different passwords in an attempt to find one that works. However, the compromised web sites in this attack are running various different kinds of software, or none at all. It is not WordPress accounts that are being compromised, but the hosting accounts themselves.
I found one account which was used for file sharing only and had the directory contents exposed, so we can see the various files placed there by spammers.
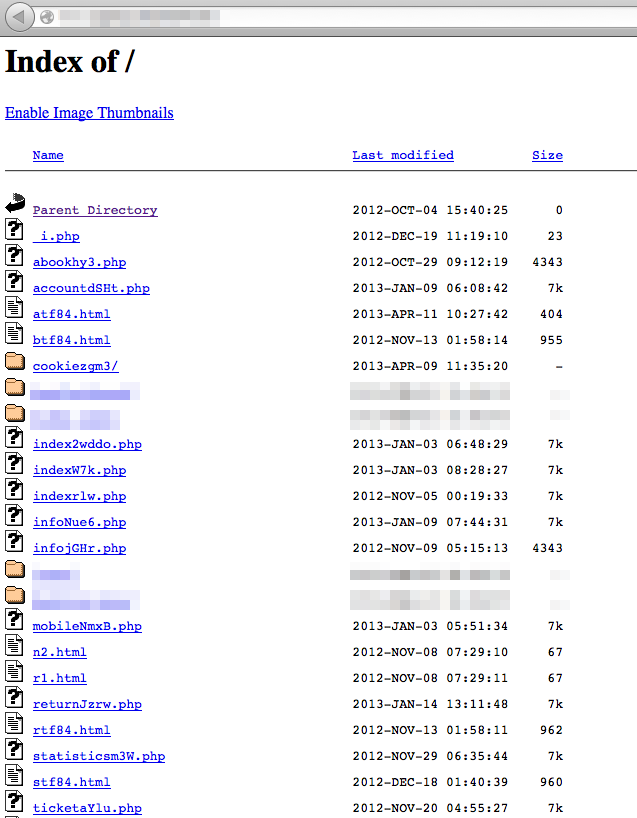 Only the file names that are fuzzed were placed there by the owner of the domain. All the ones you can see were placed there by one or more spammers. In October 2012 through January 2013 a number of .php files were created or modified. Some of these redirect to landing pages elsewhere, some were intended for sending spam, and none of them worked because PHP was not active on this server. In November 2012 and again in April this year, the same approach was tried with .html files. These do indeed redirect to spam landing pages. (n2.html and r1.html redirect to pages selling fake pharmaceuticals, and the other redirect to porn.) Finally, on April 9th, 2013, the directory cookiezgm3 was created. This contains a copy of the pornographic landing page discussed above, along with all the thumbnails, images, CSS files, and scripts.
Only the file names that are fuzzed were placed there by the owner of the domain. All the ones you can see were placed there by one or more spammers. In October 2012 through January 2013 a number of .php files were created or modified. Some of these redirect to landing pages elsewhere, some were intended for sending spam, and none of them worked because PHP was not active on this server. In November 2012 and again in April this year, the same approach was tried with .html files. These do indeed redirect to spam landing pages. (n2.html and r1.html redirect to pages selling fake pharmaceuticals, and the other redirect to porn.) Finally, on April 9th, 2013, the directory cookiezgm3 was created. This contains a copy of the pornographic landing page discussed above, along with all the thumbnails, images, CSS files, and scripts.
In fact these attacks date back further than that. A snapshot from the Wayback Machine taken in June of last year shows the site had been compromised back then. Note that the atf86.html and btf86.html files were present back then, but the files have been updated as the file size and date are different.
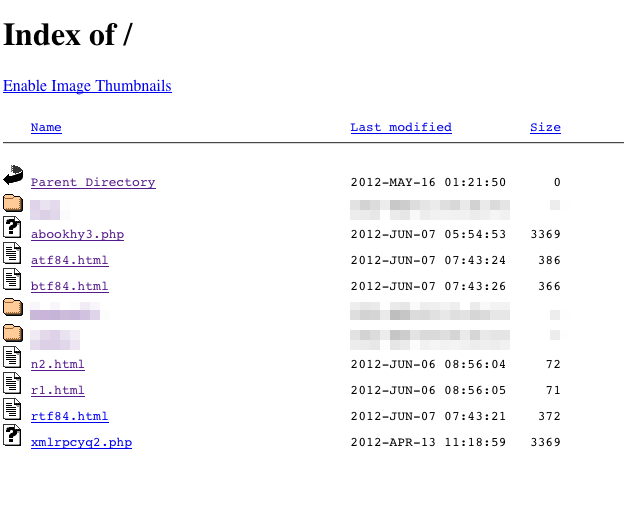 I talked to the owner of this domain to see if I could find out how it was compromised. Since PHP was not available the intruders clearly did not get in via a server side bug. My next thought was perhaps that the personal computer used to update the web page had been compromised, but it is running an up to date copy of Norton Anti-Virus. Then the owner of the domain admitted to choosing a weak password... so it looks as if the brute force attack is not limited to WordPress, but is being directed against hosting accounts as well.
I talked to the owner of this domain to see if I could find out how it was compromised. Since PHP was not available the intruders clearly did not get in via a server side bug. My next thought was perhaps that the personal computer used to update the web page had been compromised, but it is running an up to date copy of Norton Anti-Virus. Then the owner of the domain admitted to choosing a weak password... so it looks as if the brute force attack is not limited to WordPress, but is being directed against hosting accounts as well.
So far we have seen this spammer use over 30,000 different compromised domains for call to action URLs and 528 of those to also host his pornographic landing pages. It's likely many of those compromised hosting accounts are also being used to send spam. Over 20% of the emails from this spammer contain a X-PHP-Originating-Script: header indication that the email was created by a PHP script. This is generated by PHP 5.3 and above if you have the correct configuration variables set in your php.ini file. I recommend
mail.add_x_header = On
mail.log = /var/log/phpmail.log
This will log outgoing emails sent from PHP on your server and the Originating-Script header will tell you where they are coming from.
There is one more chapter to this story. We are seeing a disproportionate number of these hacked domains on two hosting services, one in the US, and one in Germany. Do these hosting services allow an unlimited number of login attempts? Or did a spammer get hold of their /etc/passwd/ file containing encrypted passwords and run a dictionary attack against that? Either way, simply using a strong password would have protected those accounts. Remember, folks, unless your spell checker underlines it, it's not a password, and hackers sp33k 1337 as well.
If you are a hosting provider, here are a few things you can do to prevent account compromise:
- Make sure your clients use strong passwords both on their hosting account and WordPress accounts - especially make sure they don't use passwords in the dictionary or on this list.
- Salt password hashes before you store them.
- Prevent unlimited login attempts, and use extra authentication if the login is from an IP address not previously seen for that account.
- Use the php.ini parameters listed above, and monitor the PHP mail log for sudden increases in volume.
- Encourage your clients to run the latest release of WordPress and Joomla.
- Hosting providers can request a free outbound spam analysis from Cloudmark. Contact Blair Bolden.



