Just when the
plague of hacked web servers seemed to be dying down a little, we hear of a
new exploit for Joomla. While we haven't seen this exploit being used by spammers yet, it will likely turn up in coming weeks. In the meantime, there are already two easy exploits in Joomla 1.5 that have been widely used. One is a SQL injection attack that allows you to reset the administrator password. The other, a bug in the JCE content manager plug-in, allows attackers to upload a fake .gif file. Then they can use the directory rename feature to change it to a .php file. Patches are available for both of these, but there are still tens of thousand of unpatched Joomla sites out there - and by now, it looks like most of them have been hacked multiple times.
This PHP code, published by a Turkish security researcher, will scan a list of domains for one of these vulnerabilities and compromise any web sites where it is found. The code isn't simply proof-of-concept either - we've seen it being used in the wild. However, it is by no means the only tool used. If a Joomla site is vulnerable, we usually see three or four different successful attacks. Several different spammers will be using the site for call to action URLs, and sometimes sending spam or hosting landing pages.
A few weeks ago, the new compromised domains we saw were predominantly Joomla 1.5, but recently the Joomla numbers are going down, and WordPress is a greater percentage of the total. The current numbers are 37% Joomla, 33% WordPress and 30% other. Unlike Joomla, WordPress provides an easy way to upgrade to the latest release. However, this does not seem to help much. WordPress 3.6 was only released a couple of weeks ago. It already accounts for 8% of all the recently compromised WP sites. The previous releases 3.5.2 and 3.5.1 account for 14% and 21% respectively.
While I was working on this article, one of my colleagues was defending against a brute force attack on the password of his personal WordPress blog. The login attempts were coming from a botnet - he saw 2,172 unique IP addresses used over the course of two and a half hours. If you have a WordPress or Joomla web site, make sure each account on it has a strong password. As well as brute force attacks, hackers can also exploit vulnerabilities in plug-ins. Even with an up-to-date release of WordPress, your website may still be exposed to an attack via a bug or even a
malicious trojan in a plug-in.
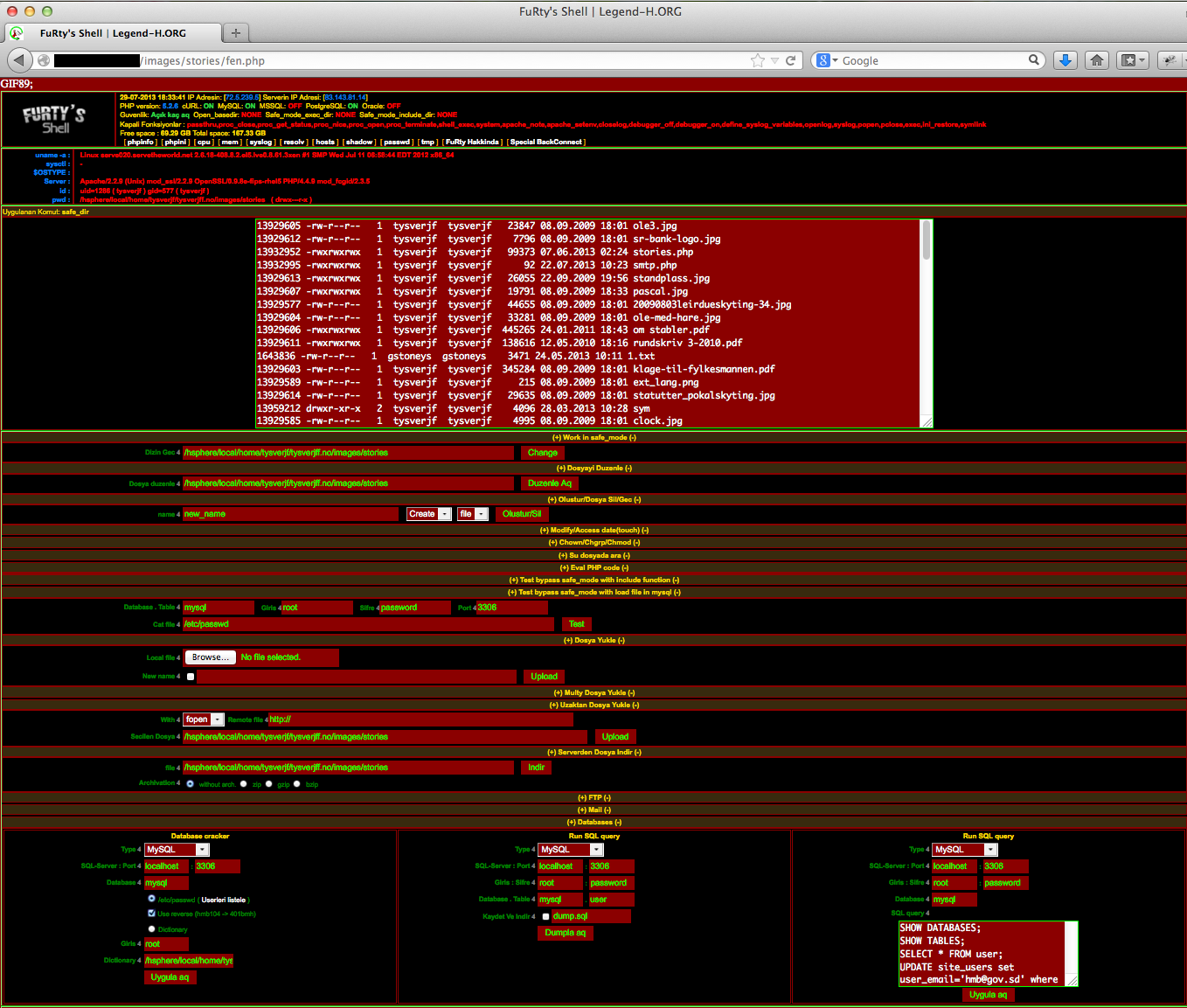
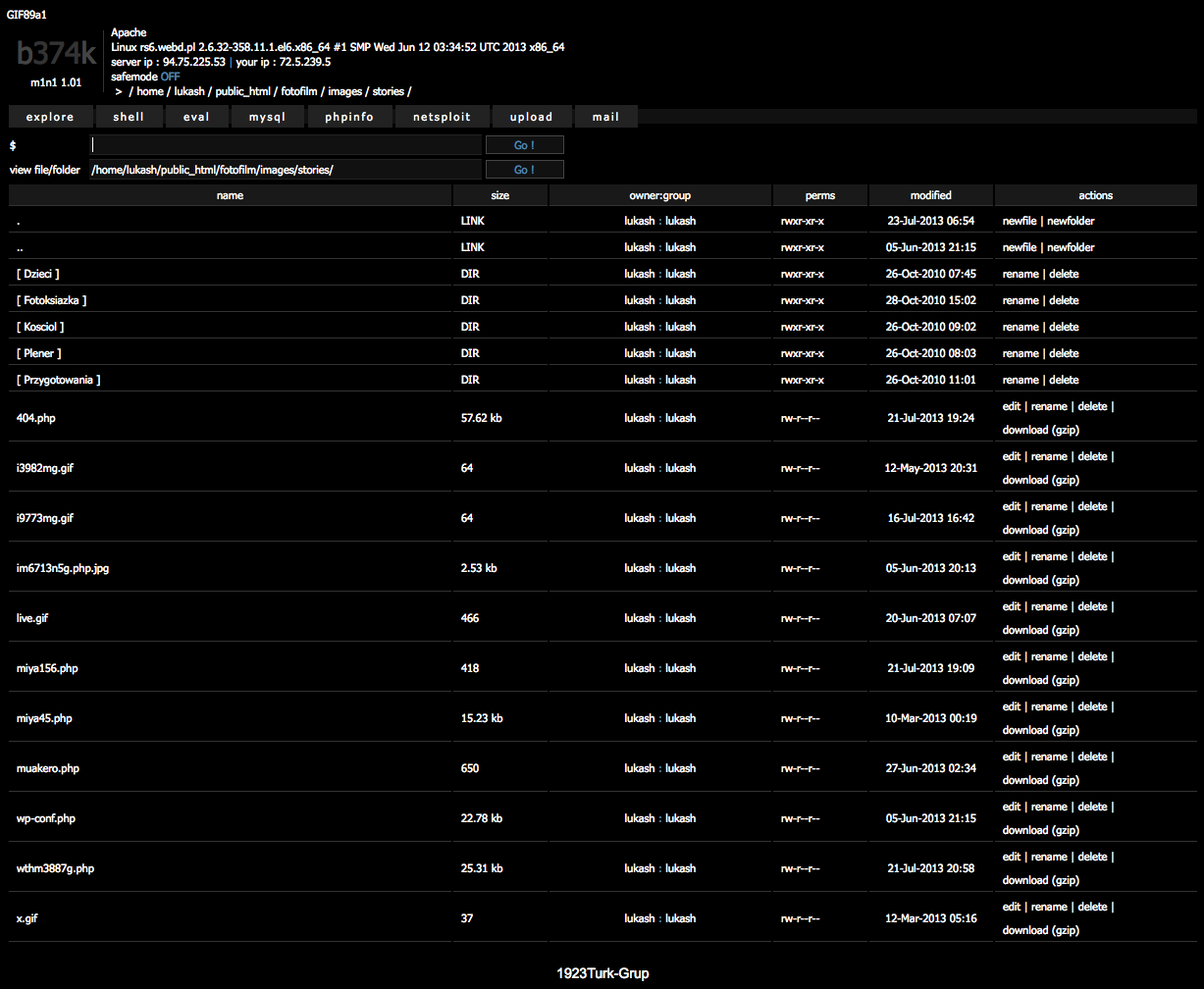
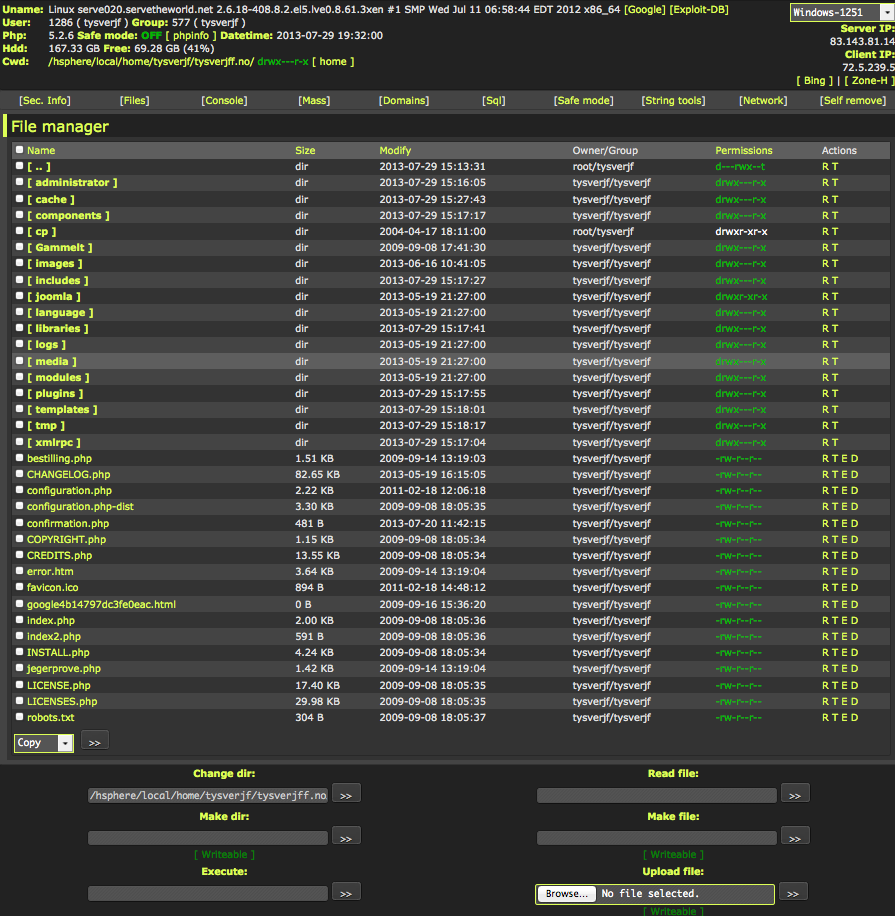
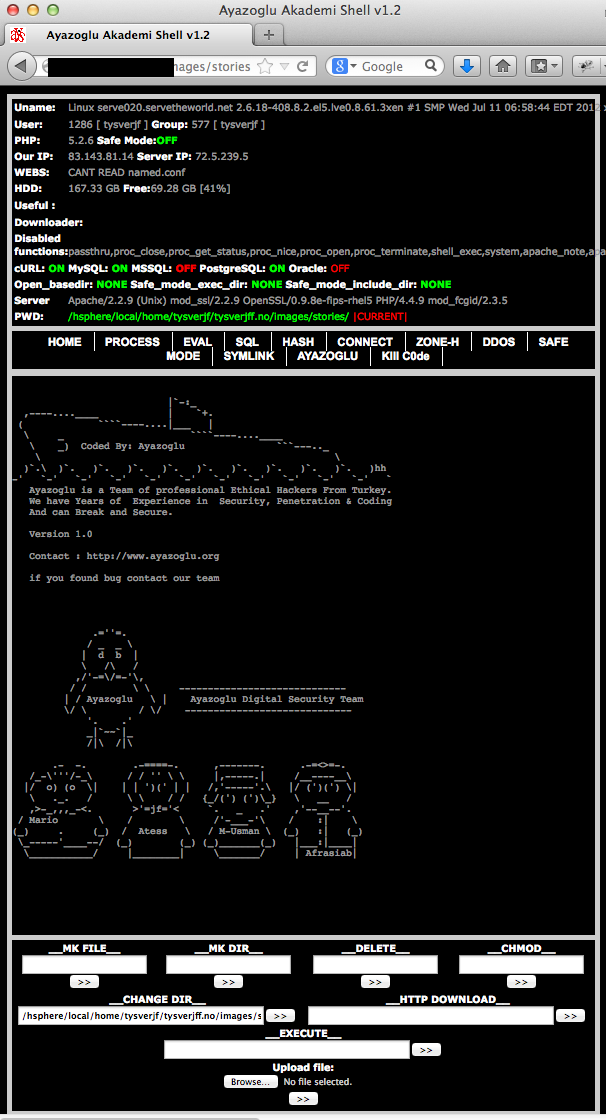
Once an account has been compromised, the hacker can then upload a PHP shell program. These give complete control over the compromised account. They allow the hacker to view, edit, delete, and create files anywhere in the file system, as well as running programs from the command line. We see other malicious programs installed to access SQL databases, launch DDoS attacks, or send spam emails. There are usually multiple shells of this sort on a single account, showing that it has been hacked by several different criminals. Below are some examples. Click on the thumbnails for full size versions.
The last shell claims to be written by a "Team of professional Ethical Hackers From Turkey," but it contains a single button for launching DDoS attacks. I'm not quite clear on the concept of an ethical DDoS attack.
That raises an interesting potential problem, though. The DDoS attack against Spamhaus earlier this year was launched by a fifteen year old kid in London armed with pretty limited resources - just half a dozen compromised servers talking to tens of thousands of open DNS resolvers. There are tens of millions of open DNS resolvers out there, and we see tens of thousands of compromised servers under the control of a single spammer. There is potential for a DDoS attack of a volume that could cause widespread disruption on the entire Internet if someone puts these resources together. I should mention that the DDoS tool in the shell above is a lot less dangerous than the one used to attack Spamhaus, as it does not use open DNS resolvers for amplification.
Apart from open DNS resolvers, the other requirement for a DNS reflection attack is that the compromised servers need to pretend to send DNS requests from the victim's IP address and not their own. Most hosting companies do not allow packets with a spoofed IP address to leave their network, but
some still do. This is an easy fix, it's only a router setting. If you are a sysadmin for any sort of network, check to see if your gateway routers are configured to allow outgoing spoofed IP addresses. If they are, fix it as soon as you can. You can download test software
here.
Though compromised domains can be used to host landing pages, act as proxies, launch DDoS attacks, or send spam emails, the most common use we see is just to provide a large supply of URLs to be used in the call to action in spam emails. We can block this spam at the URL level, but some spammers set up hundreds of URLs on a single server. Others update the .htaccess file to use Apache's mod_rewrite module to redirect any unknown URL to their landing page, giving them an infinite supply of calls to action on each web server. This has a negative effect on the reputation of the entire domain, making it possible that legitimate email from the owner of the web site will also be filtered. If 99.5% of all the email referencing a particular domain is spam, the other 0.5% is going to have a hard time getting delivered.
If you do find that your web hosting account has been hacked, remember that hackers may have left themselves with back doors to regain control of you account if you try to clean it up. The safest way to recover is to rebuild your web site on a new hosting account. Use clean installs of the latest version of all the software you use, and set up accounts with new, strong passwords. Do not copy anything from the old account except .jpeg and .gif files. If you have to migrate SQL databases to the new account, make sure that they have not been corrupted by spammers - especially if they contain user account information. Once your new site is set up, change your DNS records to point to the new location, and delete everything on the old account.